Burying your head in the sand and ignoring data encryption in software development won’t protect you from predators lurking in the shadows of the cyber world.
The real-world consequences of this neglect can be catastrophic, leading to data theft, reputation damage, and financial loss.
After a decade in cybersecurity, I can assure you that there’s a better way: prioritize data encryption from the ground up, and I’m here to guide you through it.
| Topic | Details |
|---|---|
| Importance of Data Encryption | Protects sensitive information, ensures data integrity, and prevents unauthorized access. |
| Types of Data Encryption | Symmetric encryption, asymmetric encryption, hashing, and encryption in transit and at rest. |
| Best Practices | Strong algorithms, key management, regular updates, compliance, and secure development practices. |
| Tools and Technologies | AES, RSA, TLS, SSL, and secure key management systems. |
| Role of Developers | Implement encryption, follow security guidelines, and stay updated with latest encryption standards. |
Data encryption is a cornerstone of secure software development. It ensures that sensitive information remains confidential and protected from unauthorized access, making it a critical aspect for businesses leveraging BizCoder to hire developers.
Understanding Data Encryption
Data encryption converts plain text into an unreadable format, accessible only by those who possess the decryption key. This process is essential for protecting sensitive data, whether it’s stored (at rest) or being transmitted (in transit). There are several types of encryption methods that developers should be familiar with:
Symmetric Encryption
Symmetric encryption is a cornerstone of modern cryptography, characterized by the use of a single key for both encryption and decryption processes. This method is renowned for its speed and efficiency, making it ideal for encrypting large volumes of data in real-time applications. However, its reliance on a single key for both operations necessitates robust key management practices to ensure security.
Key Characteristics of Symmetric Encryption
- Single Key Usage: In symmetric encryption, the same key is employed to both encode and decode data. This simplicity contributes to its speed, as the process of transforming plaintext into ciphertext and vice versa is straightforward and computationally less intensive compared to asymmetric encryption.
- Speed and Efficiency: Due to its less complex mathematical operations, symmetric encryption algorithms are generally faster and more efficient. This makes them suitable for scenarios where high throughput is essential, such as securing real-time communications and encrypting large datasets.
- Key Management Challenges: The primary challenge with symmetric encryption lies in key management. Since the same key is used for both encryption and decryption, it must be securely distributed and stored. If the key is compromised, the entire encryption system is at risk. Therefore, robust mechanisms for key generation, storage, and rotation are critical.
Common Symmetric Encryption Algorithms
The most prominent symmetric encryption algorithm is the Advanced Encryption Standard (AES), which has become the industry benchmark for securing data.
Advanced Encryption Standard (AES):
Algorithm Structure: AES is a block cipher that encrypts data in fixed-size blocks of 128 bits. It supports key sizes of 128, 192, and 256 bits, offering varying levels of security. The algorithm consists of multiple rounds of encryption operations, including substitution, permutation, and mixing of the data to create ciphertext.
Security and Performance: AES-256 is highly regarded for its security and is approved by the U.S. National Security Agency (NSA) for encrypting top-secret information. Its performance efficiency makes it suitable for both hardware and software implementations, ensuring rapid encryption and decryption processes without significant performance overhead.
Implementation Considerations: When implementing AES, developers should leverage well-vetted cryptographic libraries and avoid creating custom implementations, which can introduce vulnerabilities. Examples of reliable libraries include OpenSSL, Bouncy Castle, and Microsoft’s Cryptography API: Next Generation (CNG).
Best Practices for Symmetric Encryption
- Secure Key Distribution: Ensure that keys are distributed over secure channels to prevent interception. Techniques such as Diffie-Hellman key exchange or using a secure asymmetric encryption method for key exchange can enhance security during distribution.
- Key Rotation and Lifespan: Regularly rotate encryption keys to limit the amount of data encrypted with a single key. This practice minimizes the impact of a potential key compromise. Define key rotation policies and automate the process using key management systems.
- Use of Strong Keys: Generate keys using cryptographically secure random number generators (CSPRNGs) to ensure they are strong and unpredictable. Avoid using weak or easily guessable keys, and never hardcode keys into the source code.
- Storage Security: Store keys in secure environments, such as Hardware Security Modules (HSMs) or secure key management services provided by cloud providers (e.g., AWS KMS, Azure Key Vault). These solutions offer enhanced protection against unauthorized access and tampering.
- Encryption Modes and Padding: Choose appropriate encryption modes (e.g., CBC, GCM) and ensure proper padding of plaintext to maintain security and data integrity. Galois/Counter Mode (GCM) is recommended for its built-in integrity check, which provides both encryption and authentication.
Uses the same key for both encryption and decryption. It’s faster but requires secure key management. Common algorithms include AES (Advanced Encryption Standard).
Asymmetric Encryption

Image source: Bhatia, Priyanka & Sumbaly, Ronak. (2014). Framework for Wireless Network Security Using Quantum Cryptography. International journal of Computer Networks & Communications. 6. 10.5121/ijcnc.2014.6604.
Asymmetric encryption, also known as public-key cryptography, is a critical component of secure communication systems. It leverages a pair of cryptographic keys – a public key and a private key – to encrypt and decrypt data.
This dual-key mechanism enhances security, particularly for key exchange over untrusted networks, and underpins many of the protocols and systems used for secure internet communication.
Key Characteristics of Asymmetric Encryption
- Dual-Key System: Asymmetric encryption utilizes two mathematically related keys. The public key is used for encryption, and the private key is used for decryption. The public key can be shared openly without compromising security, while the private key must be kept confidential.
- Enhanced Security for Key Exchange: The separation of encryption and decryption keys makes asymmetric encryption particularly secure for exchanging keys over untrusted networks. Since only the private key can decrypt data encrypted with the public key, even if the public key is intercepted, the data remains secure.
- Complexity and Performance: Asymmetric encryption involves more complex mathematical operations than symmetric encryption, which results in slower performance. Consequently, it is often used in conjunction with symmetric encryption to balance security and efficiency. For example, asymmetric encryption can securely exchange a symmetric key, which is then used for faster bulk data encryption.
Common Asymmetric Encryption Algorithms
One of the most widely used asymmetric encryption algorithms is RSA (Rivest-Shamir-Adleman). Other notable algorithms include Elliptic Curve Cryptography (ECC) and Digital Signature Algorithm (DSA).
RSA (Rivest-Shamir-Adleman):
Algorithm Structure: RSA is based on the mathematical properties of large prime numbers and their difficulty to factorize. The security of RSA relies on the computational challenge of breaking down a large number into its prime factors, a process that is currently infeasible with classical computing resources.
Key Sizes and Security: RSA keys typically range from 2048 to 4096 bits. RSA-2048 is considered secure for most applications, while RSA-4096 offers even greater security for highly sensitive data.
Use Cases: RSA is widely used for secure data transmission, digital signatures, and key exchange. It underpins many internet security protocols, including SSL/TLS, which secures HTTPS connections.
Elliptic Curve Cryptography (ECC):
Algorithm Structure: ECC uses the properties of elliptic curves over finite fields to generate secure cryptographic keys. ECC provides comparable security to RSA but with much shorter key lengths, leading to faster computations and reduced resource usage.
Security and Efficiency: ECC-256 offers similar security to RSA-3072, making it an attractive choice for environments with limited computational power and bandwidth, such as mobile devices and IoT.
Use Cases: ECC is used in SSL/TLS, digital signatures, and key exchange mechanisms. It is also favored in blockchain technologies and cryptocurrencies for its efficiency and security.
Digital Signature Algorithm (DSA):
Algorithm Structure: DSA is primarily used for generating digital signatures rather than encrypting data. It ensures data integrity and authenticity by allowing the recipient to verify that the message was signed by the sender and has not been altered.
Below is a Python code sample demonstrating how to generate and verify a digital signature using the cryptography library in Python.
Prerequisites
Make sure you have the cryptography library installed. You can install it using pip:
pip install cryptographyCode Sample: Generating and Verifying a Digital Signature with DSA
from cryptography.hazmat.primitives import hashes
from cryptography.hazmat.primitives.asymmetric import dsa
from cryptography.hazmat.primitives.asymmetric import utils
from cryptography.hazmat.primitives import serialization
# Generate DSA private and public keys
private_key = dsa.generate_private_key(
key_size=2048 # You can use 2048 or 3072 bits as per your security requirements
)
public_key = private_key.public_key()
# Message to be signed
message = b"Important message for digital signing"
# Sign the message
signature = private_key.sign(
message,
hashes.SHA256() # DSA allows SHA-1, SHA-224, SHA-256, SHA-384, and SHA-512
)
print("Signature:", signature.hex())
# Serialize and save the public key for verification
public_key_pem = public_key.public_bytes(
encoding=serialization.Encoding.PEM,
format=serialization.PublicFormat.SubjectPublicKeyInfo
)
with open("public_key.pem", "wb") as f:
f.write(public_key_pem)
# Verification of the signature
# Load the public key
with open("public_key.pem", "rb") as f:
loaded_public_key = serialization.load_pem_public_key(f.read())
try:
loaded_public_key.verify(
signature,
message,
hashes.SHA256()
)
print("Signature is valid.")
except Exception as e:
print("Signature is invalid:", e)
Explanation
Key Generation:
The DSA private key is generated using dsa.generate_private_key with a specified key size (2048 or 3072 bits).
The corresponding public key is derived from the private key.
Signing the Message:
The message is signed using the private key’s sign method, which takes the message and the hash algorithm as parameters. In this example, hashes.SHA256 is used.
Serializing the Public Key:
The public key is serialized to PEM format and saved to a file for later use in signature verification.
Verifying the Signature:
The public key is loaded from the PEM file.
The verify method of the public key is used to verify the signature against the original message and the hash algorithm.
This code provides a basic example of generating and verifying a digital signature using DSA. In a real-world application, ensure secure key storage and handle exceptions and errors appropriately for production security practices.
Use Cases: DSA is used in digital certificates and secure email communications to authenticate and verify the integrity of messages.
Best Practices for Implementing Asymmetric Encryption
- Choose Appropriate Key Sizes: Select key sizes that provide adequate security without unnecessary performance overhead. For RSA, use at least 2048-bit keys, while ECC can achieve high security with 256-bit keys.
- Secure Key Storage: Store private keys securely using Hardware Security Modules (HSMs) or secure key management services. Ensure that private keys are not exposed to unauthorized access and are stored in tamper-proof environments.
- Key Rotation and Lifespan: Implement regular key rotation policies to minimize the impact of a potential key compromise. Define key expiration periods and automate the key rotation process to maintain ongoing security.
- Certificate Management: Utilize Public Key Infrastructure (PKI) to manage digital certificates and public keys. Ensure proper issuance, revocation, and renewal of certificates to maintain trust in your cryptographic systems.
- Hybrid Encryption Systems: Combine asymmetric and symmetric encryption to leverage the strengths of both methods. Use asymmetric encryption to securely exchange symmetric keys, which are then used for efficient data encryption.
- Implementation Best Practices: Use well-established cryptographic libraries and frameworks, such as OpenSSL, Bouncy Castle, or Microsoft’s Cryptography API: Next Generation (CNG). Avoid custom cryptographic implementations, which can introduce vulnerabilities.
Tools and Technologies for Asymmetric Encryption
- RSA: Widely supported in cryptographic libraries and tools, RSA is essential for secure communications and key exchange.
- ECC: Increasingly adopted for its efficiency and strong security, ECC is implemented in modern cryptographic systems and protocols.
- Digital Signature Algorithms: Used for signing and verifying digital documents and messages, ensuring integrity and authenticity.
Utilizes a pair of keys – a public key for encryption and a private key for decryption. It’s more secure for exchanging keys over untrusted networks. RSA (Rivest-Shamir-Adleman) is a widely used asymmetric algorithm.
Hashing
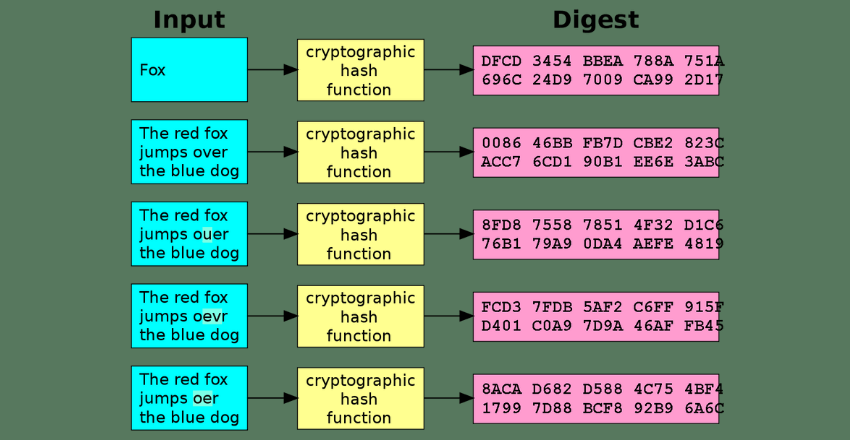
Image Source: Cryptographic hash function – Wikipedia
Hashing is a fundamental concept in cryptography and data security, playing a critical role in ensuring data integrity and authenticity. Unlike encryption, which is a reversible process, hashing transforms data into a fixed-size string of characters, known as a hash value or digest, that cannot be reversed to its original form. This irreversibility is what makes hashing particularly valuable for data verification and integrity checks.
Key Characteristics of Hashing
- Fixed-Size Output: Regardless of the size or length of the input data, hashing algorithms produce a fixed-size hash value. For example, the SHA-256 algorithm always produces a 256-bit (32-byte) hash value, whether the input is a single character or a large file.
- Deterministic Process: The hashing process is deterministic, meaning the same input will always produce the same hash value. This property is essential for verifying data integrity, as even a minor change in the input data will result in a drastically different hash value.
- Irreversibility: Hash functions are designed to be one-way functions, making it computationally infeasible to revert the hash value to its original input. This ensures that the hash value can be used as a secure representation of the original data without revealing the data itself.
- Collision Resistance: A good hash function minimizes the likelihood of two different inputs producing the same hash value, known as a collision. High collision resistance is crucial for maintaining the integrity and uniqueness of hash values.
Common Hashing Algorithms
Several hashing algorithms are widely used in various applications, each offering different levels of security and performance.
SHA-256 (Secure Hash Algorithm 256-bit):
Algorithm Structure: SHA-256 is part of the SHA-2 family, developed by the National Security Agency (NSA). It processes data in 512-bit blocks and generates a 256-bit hash value.
Security and Performance: SHA-256 is highly secure and widely used for various applications, including digital signatures, certificate validation, and blockchain technology. Its strong collision resistance and computational efficiency make it a standard choice for security-critical applications.
Use Cases: SHA-256 is extensively used in cryptocurrency systems like Bitcoin for transaction verification and in SSL/TLS for securing internet communications.
SHA-3:
Algorithm Structure: SHA-3 is the latest member of the Secure Hash Algorithm family, designed as a resilient alternative to SHA-2. It uses a sponge construction process and can generate hash values of varying lengths (224, 256, 384, and 512 bits).
Security and Performance: SHA-3 offers enhanced security features and is resistant to different types of cryptographic attacks. It is particularly suitable for applications requiring high security levels and future-proofing against advances in cryptanalysis.
Use Cases: SHA-3 is used in emerging security applications and is being adopted for secure data storage, digital signatures, and authentication protocols.
MD5 (Message Digest Algorithm 5):
Algorithm Structure: MD5 produces a 128-bit hash value from an input of any length. It processes data in 512-bit blocks, applying a series of bitwise operations, modular additions, and compression functions.
Security and Performance: Although MD5 was widely used in the past, it is now considered cryptographically broken and unsuitable for further use due to its vulnerability to collision attacks.
Use Cases: Despite its weaknesses, MD5 is still used for non-cryptographic purposes, such as checksums for data integrity verification and file transfer error detection.
Best Practices for Implementing Hashing
- Choosing the Right Algorithm: Select a hashing algorithm that meets the security requirements of your application. Avoid outdated algorithms like MD5 and SHA-1, which are vulnerable to collision attacks. Use stronger algorithms like SHA-256 or SHA-3 for robust security.
- Salting Hashes: When hashing sensitive data such as passwords, always add a unique, random salt to each input before hashing. Salting ensures that identical inputs produce different hash values, mitigating the risk of rainbow table attacks.
- Peppering Hashes: In addition to salting, use a secret value known only to the application (a pepper) that is added to the input before hashing. This adds an extra layer of security and makes precomputed attack vectors like rainbow tables ineffective.
- Iterative Hashing (Key Stretching): For sensitive data like passwords, use iterative hashing techniques such as PBKDF2, bcrypt, or Argon2. These methods repeatedly hash the input with the salt and pepper, making brute-force attacks computationally expensive and time-consuming.
- Regular Security Audits: Periodically review and update your hashing implementations to ensure they adhere to the latest security standards and best practices. Conduct security audits and penetration testing to identify and address potential vulnerabilities.
Tools and Technologies for Hashing
- OpenSSL: A widely used library that provides various cryptographic functions, including hashing algorithms like SHA-256 and SHA-3. It is a standard tool for securing web communications and data integrity.
- bcrypt: A password hashing function that incorporates salting and iterative hashing to provide strong protection against brute-force attacks. It is commonly used in web applications for storing user passwords securely.
- Argon2: The winner of the Password Hashing Competition (PHC) and considered one of the most secure password hashing algorithms. Argon2 provides configurable memory and time cost parameters to enhance security.
Converts data into a fixed-size string of characters, which is irreversible. Hashing is often used for verifying data integrity.
Encryption in Transit and at Rest

Ensuring the security of data both during transmission and while stored is paramount. Encryption in transit and at rest are two fundamental practices that safeguard data from unauthorized access and breaches. Implementing robust encryption strategies for both scenarios is crucial for maintaining data integrity, confidentiality, and compliance with regulatory standards.
Encryption in Transit
Encryption in transit, also known as transport encryption, protects data as it moves between endpoints. This type of encryption ensures that data remains confidential and unaltered as it traverses various networks, such as the internet, internal company networks, or between cloud services.
Secure Protocols: Use well-established encryption protocols to secure data in transit. These include:
TLS (Transport Layer Security): TLS is the most widely used protocol for securing data transmitted over the internet. It provides end-to-end encryption for web communications, ensuring data integrity and privacy. TLS is used in HTTPS (HTTP Secure), which encrypts web traffic between a user’s browser and the web server.
SSL (Secure Sockets Layer): SSL is the predecessor to TLS and is considered less secure. While some legacy systems still use SSL, it is recommended to upgrade to TLS to ensure robust security.
IPsec (Internet Protocol Security): IPsec is a suite of protocols used to secure Internet Protocol (IP) communications by authenticating and encrypting each IP packet in a data stream. It is commonly used for VPNs (Virtual Private Networks) to secure remote access and inter-network communications.
SSH (Secure Shell): SSH is a protocol for secure remote login and other secure network services over an insecure network. It encrypts data between a client and a server, providing confidentiality and integrity.
Certificate Management: Use digital certificates to authenticate the identities of communicating parties and establish encrypted connections. Certificates are issued by trusted Certificate Authorities (CAs) and are essential for establishing trust in TLS/SSL communications.
Public Key Infrastructure (PKI): Implement a PKI to manage digital certificates and public keys. PKI supports the creation, distribution, renewal, and revocation of certificates, ensuring secure key management and authentication processes.
Perfect Forward Secrecy (PFS): Implement PFS to ensure that session keys used for encryption are not compromised even if the server’s private key is exposed. PFS generates unique session keys for each communication session, providing an additional layer of security.
Regular Protocol Updates: Keep encryption protocols and libraries up to date to protect against known vulnerabilities and exploits. Regularly review and update configurations to adhere to the latest security standards and best practices.
Encryption at Rest
Encryption at rest protects data stored on disks or other storage media from unauthorized access. This type of encryption is crucial for safeguarding sensitive information against breaches, especially in cases of physical theft or unauthorized access to storage systems.
Full Disk Encryption (FDE): Encrypts the entire disk, ensuring that all data stored on the disk is protected. FDE is typically implemented at the hardware level, using technologies such as:
BitLocker (Windows): BitLocker is a full disk encryption feature available in Windows that uses AES encryption to protect data on the entire disk.
FileVault (macOS): FileVault is a full disk encryption program for macOS that encrypts the contents of the entire drive using XTS-AES-128 encryption.
File-Level Encryption: Encrypts individual files or directories, providing granular control over which data is encrypted. This approach allows for selective encryption of sensitive files while leaving other data unencrypted for performance reasons.
GNU Privacy Guard (GPG): GPG is an encryption software that uses the OpenPGP standard to encrypt and sign files and communications. It provides robust file-level encryption for various operating systems.
Database Encryption: Protects sensitive data stored in databases by encrypting data at the column or table level. Database encryption can be implemented using built-in database features or third-party tools.
Transparent Data Encryption (TDE): TDE encrypts database files at the file level, making it transparent to applications and users. It is available in various database systems, such as Microsoft SQL Server, Oracle, and MySQL.
Encryption Key Management: Proper management of encryption keys is essential for maintaining the security of encrypted data at rest. Use secure key management solutions to generate, store, rotate, and revoke encryption keys.
Hardware Security Modules (HSMs): HSMs are physical devices that provide secure key storage and management. They protect keys from unauthorized access and tampering, ensuring the integrity and confidentiality of encrypted data.
Key Management Services (KMS): Cloud-based KMS solutions, such as AWS KMS or Azure Key Vault, offer scalable and secure key management for cloud environments. These services automate key rotation and provide centralized management of encryption keys.
Best Practices for Implementing Encryption

- Use Strong Encryption Algorithms: Employ industry-standard encryption algorithms such as AES-256 for data at rest and TLS 1.2 or 1.3 for data in transit. Avoid using deprecated algorithms like DES or RC4, which are vulnerable to attacks.
- Implement Multi-Factor Authentication (MFA): Enhance security by requiring multiple forms of authentication for accessing encrypted data. MFA adds an additional layer of protection, making it more difficult for unauthorized users to access sensitive information.
- Regularly Update and Patch Systems: Keep encryption software, libraries, and hardware up to date with the latest security patches and updates. Regular maintenance helps protect against newly discovered vulnerabilities and exploits.
- Conduct Security Audits and Penetration Testing: Regularly audit encryption implementations and conduct penetration testing to identify and address potential weaknesses. Security audits ensure compliance with industry standards and regulatory requirements.
- Educate and Train Staff: Provide ongoing training for staff on encryption best practices and data security. Ensuring that employees understand the importance of encryption and how to implement it correctly is crucial for maintaining a secure environment.
Tools and Technologies for Encryption
- OpenSSL: A robust and widely used library that provides various cryptographic functions, including encryption for data in transit and at rest.
- VeraCrypt: An open-source disk encryption software that provides on-the-fly encryption for data at rest, supporting various encryption algorithms.
- AWS Key Management Service (KMS): A cloud-based service for managing encryption keys in the AWS environment, providing secure and scalable key management.
Ensures data is encrypted while being transferred across networks and when stored on disk.
Best Practices for Data Encryption
To implement effective data encryption, developers should adhere to several best practices:
Use Strong Algorithms: Employ industry-standard encryption algorithms like AES-256 for symmetric encryption and RSA-2048 for asymmetric encryption. AES-256 is favored for its long key length, which provides robust protection against brute-force attacks. RSA-2048 is widely used due to its strong security for key exchange. These algorithms are recognized for their robustness, efficiency, and widespread acceptance in the industry.
Secure Key Management: Proper management of encryption keys is crucial. Use secure key management systems, such as Hardware Security Modules (HSMs) and cloud-based solutions like AWS Key Management Service (KMS) or Azure Key Vault, to generate, store, and rotate keys. Ensure keys are never hardcoded into the source code. Implement multi-factor authentication for accessing keys and establish clear key rotation policies to mitigate the risk of key compromise.
Regularly Update Encryption Protocols: Encryption standards evolve over time. Regularly update protocols and libraries to incorporate the latest security improvements and patches. Monitor industry developments and emerging threats to stay ahead of potential vulnerabilities. Utilize automated tools for tracking and applying security updates.
Compliance with Regulations: Adhere to relevant data protection regulations such as GDPR, HIPAA, and CCPA. Ensure encryption practices meet these legal requirements to avoid potential penalties. Achieve certifications like FIPS 140-2, which sets the standard for cryptographic modules, to demonstrate compliance and build trust with clients.
Secure Development Practices: Incorporate security into every phase of the development lifecycle. Conduct regular code reviews, security audits, and penetration testing to identify and mitigate vulnerabilities. Follow secure coding standards, such as those outlined by the OWASP Foundation, to prevent common security flaws. Implement continuous integration/continuous deployment (CI/CD) pipelines with integrated security checks to ensure ongoing compliance and protection.
Tools and Technologies

Developers can leverage various tools and technologies to implement data encryption effectively:
- AES (Advanced Encryption Standard): A symmetric encryption algorithm widely used for its efficiency and security.
- RSA (Rivest-Shamir-Adleman): An asymmetric encryption algorithm used for secure data transmission.
- TLS/SSL (Transport Layer Security/Secure Sockets Layer): Protocols that ensure secure communication over networks.
- Secure Key Management Systems: Solutions like AWS Key Management Service (KMS) and Azure Key Vault provide secure key storage and management.
- Hardware Security Modules (HSMs): Devices that provide physical and logical protection of keys from unauthorized access and use.
Emerging Trends in Data Encryption
- Post-Quantum Cryptography: As quantum computing advances, traditional encryption algorithms may become vulnerable. Post-quantum cryptography aims to develop algorithms that can withstand quantum attacks, ensuring long-term data security.
- Homomorphic Encryption: This technique allows computations on encrypted data without decrypting it, preserving privacy while enabling data processing and analysis.
- Blockchain-Based Encryption: Leveraging blockchain technology for decentralized and immutable encryption key management offers a promising approach to enhance security and transparency.